Port Roles & User management
Port's RBAC mechanism makes it possible to assign permissions to specific users and teams, as well as configure custom roles tailored to the needs of the different personas in Port.
Assigning permissions
In Port, you can assign permissions by using roles, team ownership and users.
Roles
There are 3 types of roles. Below are their out-of-the-box permissions:
| Role | Description |
|---|---|
| Admin | Perform any operation on the platform |
| Moderator of a Blueprint | Perform any operation on a specific blueprint and its entities. A user can be a moderator of multiple blueprints |
| Member | Read-only permissions + permissions to execute actions |
The Moderator role is automatically created during blueprint creation.
For example, creating the blueprint Env will generate a role named Env-moderator, which can perform any operation on the Env blueprint and its entities.
Hierarchy
In addition to the permissions designated for each role, permissions are also inherited based on the following hierarchy:
Admin > Moderator > Member
For example, if Members are allowed to edit Cluster entities, then Microservices Moderators are also allowed to edit them (Admins can edit all entities under all blueprints).
You can view (and edit) each user’s role in the users table:
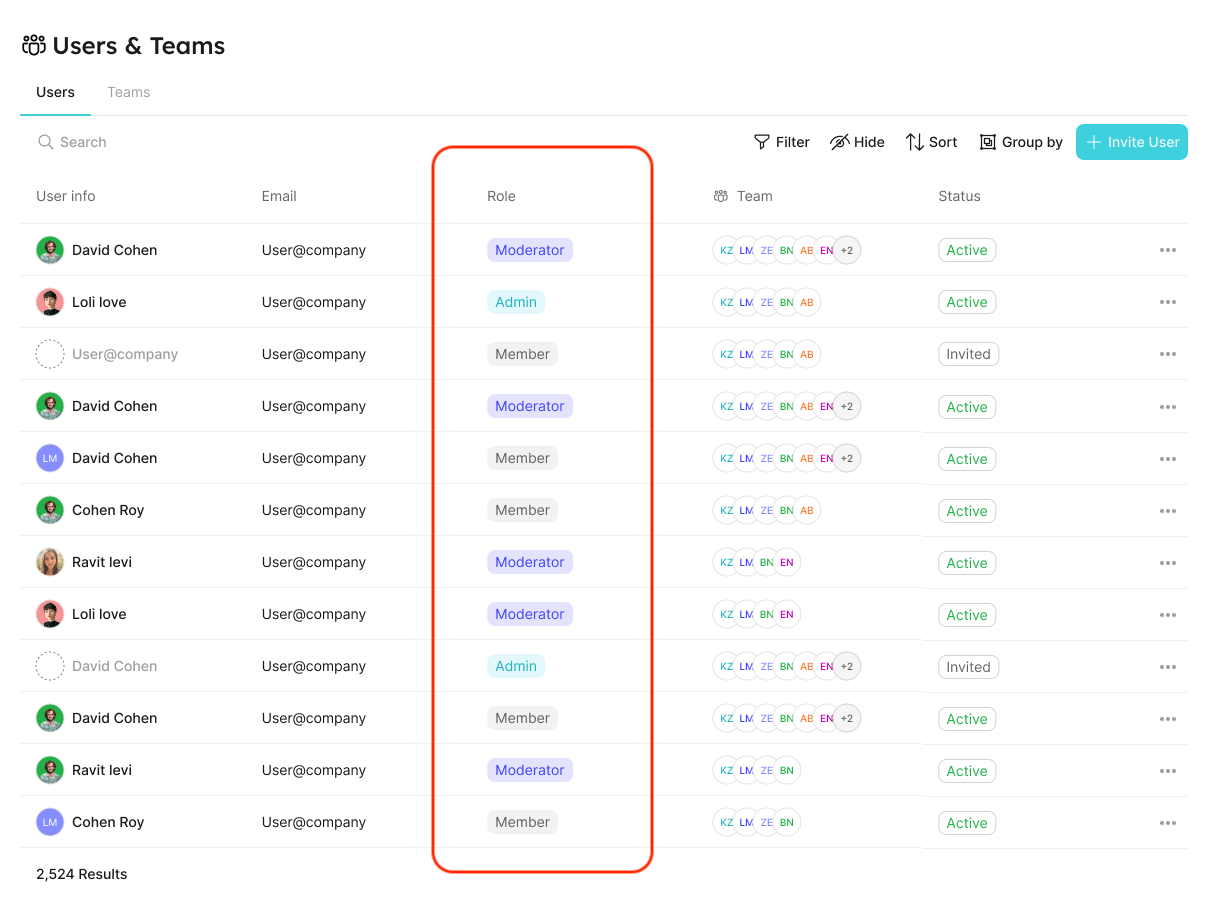
Refer to the Users and Teams section for more information about the users page
Users and Teams management
In Port, you can control and manage all your users and teams, in one place.
This allows admins to:
- Invite users to their organization and assign them specific roles and teams.
- Manage teams and their members.
- Promote ownership of assets within the organization (with team assignments).
- Set granular permissions on the portal (permission management).
It will also benefit developers, who could:
- Know what software assets they own and are responsible for.
- View and perform actions on their assets, according to their role and team.
Each user is defined by the following properties:
- Basic information - image, name, and email.
- Role - the user’s permissions level (see the set catalog RBAC section);
- Teams - a
teamis a group of users that owns Entities (see the team section).
Users and teams can be managed via:
- The Users & Teams page
- Port's Terraform provider
- The Port API
Users & Teams Page
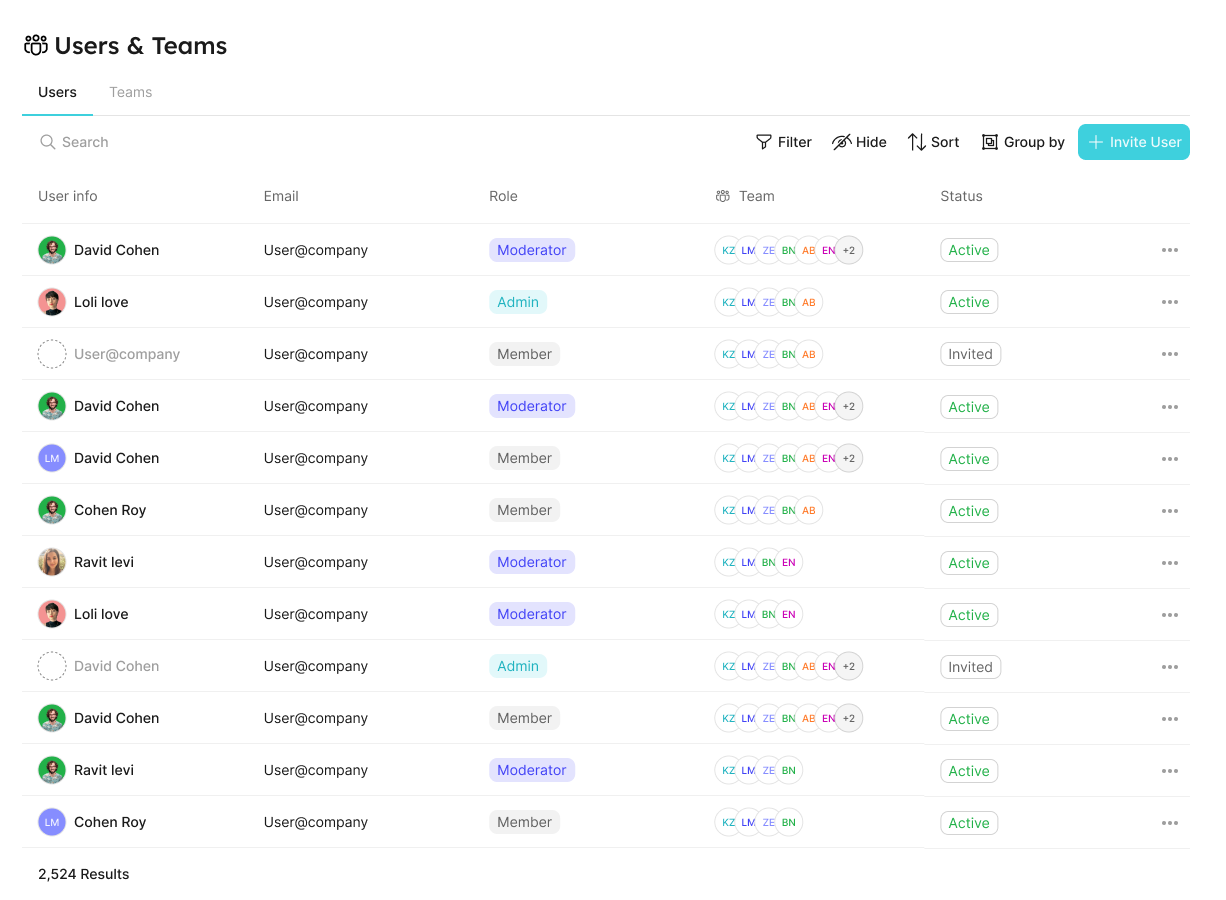
Users tab
In the users tab, you can:
- View all users.
- Invite new users.
- Edit users.
- Delete users.
Teams tab
In the teams tab, you can:
- View all teams.
- Create new teams.
- Edit teams.
- Delete teams.
Note: the following limitations do not apply to teams created manually inside Port.
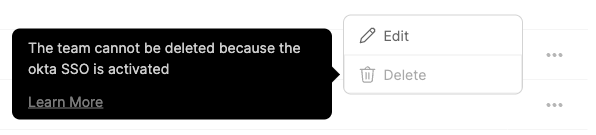
When Single Sign-On (SSO) is enabled, users and teams information (including team membership) is taken directly from your identity provider (IdP).
Since those teams are synced from your IdP the following actions cannot be performed on them:
- Edit SSO team membership;
- Delete SSO teams.
If you try to perform one of the disabled actions, the interface will display an explanation:
Terraform provider
You can perform the aforementioned actions via the Terraform provider.
Here is a basic example of a main.tf file that defines a team with 3 users:
resource "port_team" "example" {
name = "example"
description = "example"
users = [
"user1@test.com",
"user2@test.com",
"user3@test.com",
]
}
You can browse the team schema here.
Port API
The API allows you to manage teams and users.
Team meta property
Each entity has a meta-property called team, that allows you to set which team owns the entity. As an admin, you can also set blueprint permissions according to this field.
Entity JSON example with team field:
{
"identifier": "unique-ID",
"title": "Entity Title",
"team": [],
"blueprint": "testBlueprint",
"properties": {
"prop1": "value"
},
"relations": {}
}
Team dropdown selector in the entity create/edit page:
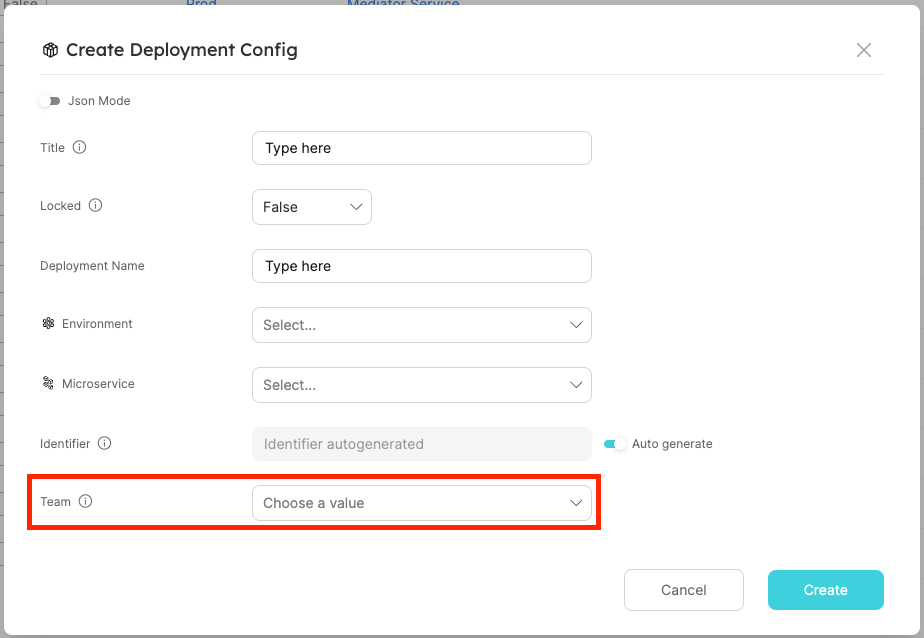
| Field | Type | Description | Default |
|---|---|---|---|
| team | List | System field that defines the team that owns an Entity | "team": [] |
- We support the manual creation of teams on Port, as well as integrating with identity providers, such as Okta and AzureAD, to import existing teams.
- When users log in to Port, their groups will be pulled automatically from their identity provider, and the allowed team values will be updated accordingly.
- It is also possible to configure team inheritance and utilize relations to auto-populate the
teamkey of entities.
Okta and AzureAD integrations are only available after configuring SSO from the relevant identity provider, refer to the Single Sign-On (SSO) section for more details
Users and teams as blueprints
Port allows you to manage users and teams as blueprints.
This option is disabled by default, and can be enabled via Port's API.
After enabling this option, two new blueprints will be created in your data model - User and Team.
These blueprints represent Port users and teams, and their data will be synced accordingly:
- When you create a user/team entity, a matching Port user/team will be created as well.
- When you delete a user/team entity, the matching Port user/team will be deleted as well.
The syncing mechanism is bidirectional, meaning that every create/edit/delete action performed on a user/team will be reflected in the entities as well.
Why manage users and teams as blueprints?
With this powerful feature you can accomplish the following:
- Enrich your users and teams data by adding properties to these blueprints - Slack URLs, titles, profiles, or any other data.
- Enrich your users and teams data by adding relations to these blueprints - for example, you can relate a user to a domain, or a team to a project.
- As with all other blueprints, you can ingest data into your entities using an integration. For example, you can map your GitHub users into Port users via your GitHub integration configuration.
The User and Team blueprints cannot be deleted or edited, and their default properties cannot be changed.
You can, however, create new properties and relations in them and edit/delete them as you wish.
Enable option
To enable management of users and teams as blueprints, send a POST request to a designated endpoint:
curl -L -X POST 'https://api.getport.io/v1/blueprints/system/user-and-team' \
-H 'Authorization: <YOUR_BEARER_TOKEN>'
- Go to your Port application, click on the
...button in the top right corner, and selectCredentials. - Click on the
Generate API tokenbutton, and copy the generated token.