Set catalog RBAC
Port provides granular control to ensure that every user only sees the parts of the catalog that are relevant for them.
Port's catalog RBAC capabilities are enabled by utilizing permissions controls.
In order to manage who can view certain pages in Port, check out page permissions.
Common Catalog RBAC usage
Catalog RBAC allows admins to finely control which users have access to specific information in the software catalog, for example:
- Allow a user to edit a single specific property on an entity.
- Create a fully read-only view for a developer.
Set global access controls to catalog data
The default permissions assigned to every blueprint upon creation specify that users with the admin role, and users with the specific blueprint moderator role, can perform any action on a blueprint.
See RBAC permissions for more information about the different roles.
It is possible to assign global permissions controls on entities, using these steps:
-
Go to the Builder page of your portal.
-
Select your desired blueprint, click on the
...button in the top-right corner, and selectPermissions: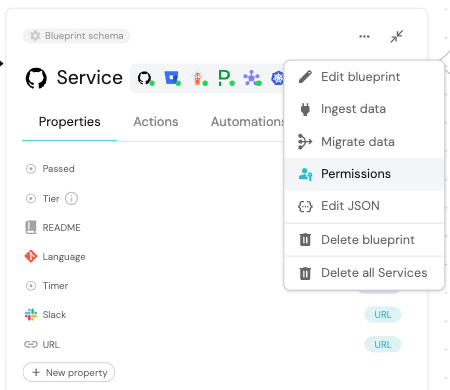
-
A JSON editor will open, where you can set the permissions for the blueprint.
- Read
- Create (register)
- Update
- Delete (unregister)
To assign permissions to read (view) an entity, give the desired persona permissions under the read object as shown below:
- Role
- User
- Team
- Ownership
To give read permissions to another role, add it to the roles array:
{
"entities": {
... other permissions
"read": {
"roles": ["my-blueprint-moderator", "Admin", "my-role"], // added my-role
"users": [],
"teams": [],
"ownedByTeam": false
}
}
}
To give read permissions to another user, add it to the users array:
{
"entities": {
... other permissions
"register": {
"roles": ["my-blueprint-moderator", "Admin"],
"users": ["my-user@example.com"], // added my-user@example.com
"teams": [],
"ownedByTeam": false
}
}
}
To give read permissions to another team, add it to the teams array:
{
"entities": {
... other permissions
"register": {
"roles": ["my-blueprint-moderator", "Admin"],
"users": [],
"teams": ["my-team"], // added my-team
"ownedByTeam": false
}
}
}
Teams can be assigned to entities, denoting the team's ownership of the entity.
To give read permissions to members of the owning team of an entity, change the ownedByTeam key:
{
"entities": {
... other permissions
"register": {
"roles": ["my-blueprint-moderator", "Admin"],
"users": [],
"teams": [],
"ownedByTeam": true // changed from false
}
}
}
Note that assigning create, update, or delete permissions to a user or team will automatically grant them read permissions as well, as they need to be able to see the entities they are allowed to interact with.
Setting read permissions on entities takes effect at the API level, meaning that any component in Port that fetches entities will be affected by these permissions.
For example, a table widget that displays entities will only show entities that the user has read permissions for.
To assign permissions to create an entity, give the desired persona permissions under the register object as shown below:
- Role
- User
- Team
- Ownership
To give create permissions to another role, add it to the roles array:
{
"entities": {
... other permissions
"register": {
"roles": ["my-blueprint-moderator", "Admin", "my-role"], // added my-role
"users": [],
"teams": [],
"ownedByTeam": false
}
}
}
To give create permissions to another user, add it to the users array:
{
"entities": {
... other permissions
"register": {
"roles": ["my-blueprint-moderator", "Admin"],
"users": ["my-user@example.com"], // added my-user@example.com
"teams": [],
"ownedByTeam": false
}
}
}
To give create permissions to another team, add it to the teams array:
{
"entities": {
... other permissions
"register": {
"roles": ["my-blueprint-moderator", "Admin"],
"users": [],
"teams": ["my-team"], // added my-team
"ownedByTeam": false
}
}
}
Teams can be assigned to entities, denoting the team's ownership of the entity.
To give create permissions to members of the owning team of an entity, change the ownedByTeam key:
{
"entities": {
... other permissions
"register": {
"roles": ["my-blueprint-moderator", "Admin"],
"users": [],
"teams": [],
"ownedByTeam": true // changed from false
}
}
}
In the context of the create permission, owned by team means that a user can only create a new entity if he assigns to it a team that he is a member of.
To assign permissions to update an entity, give the desired persona permissions under the update object as shown below:
- Role
- User
- Team
- Ownership
To give update permissions to another role, add it to the roles array:
{
"entities": {
... other permissions
"update": {
"roles": ["my-blueprint-moderator", "Admin", "my-role"], // added my-role
"users": [],
"teams": [],
"ownedByTeam": false
}
}
}
To give update permissions to another user, add it to the users array:
{
"entities": {
... other permissions
"update": {
"roles": ["my-blueprint-moderator", "Admin"],
"users": ["my-user@example.com"], // added my-user@example.com
"teams": [],
"ownedByTeam": false
}
}
}
To give update permissions to another team, add it to the teams array:
{
"entities": {
... other permissions
"update": {
"roles": ["my-blueprint-moderator", "Admin"],
"users": [],
"teams": ["my-team"], // added my-team
"ownedByTeam": false
}
}
}
Teams can be assigned to entities, denoting the team's ownership of the entity.
To give update permissions to members of the owning team of an entity, change the ownedByTeam key:
{
"entities": {
... other permissions
"update": {
"roles": ["my-blueprint-moderator", "Admin"],
"users": [],
"teams": [],
"ownedByTeam": true // changed from false
}
}
}
To assign permissions to delete an entity, give the desired persona permissions under the delete object as shown below:
- Role
- User
- Team
- Ownership
To give delete permissions to another role, add it to the roles array:
{
"entities": {
... other permissions
"unregister": {
"roles": ["my-blueprint-moderator", "Admin", "my-role"], // added my-role
"users": [],
"teams": [],
"ownedByTeam": false
}
}
}
To give delete permissions to another user, add it to the users array:
{
"entities": {
... other permissions
"unregister": {
"roles": ["my-blueprint-moderator", "Admin"],
"users": ["my-user@example.com"], // added my-user@example.com
"teams": [],
"ownedByTeam": false
}
}
}
To give delete permissions to another team, add it to the teams array:
{
"entities": {
... other permissions
"unregister": {
"roles": ["my-blueprint-moderator", "Admin"],
"users": [],
"teams": ["my-team"], // added my-team
"ownedByTeam": false
}
}
}
Teams can be assigned to entities, denoting the team's ownership of the entity.
To give delete permissions to members of the owning team of an entity, change the ownedByTeam key:
{
"entities": {
... other permissions
"unregister": {
"roles": ["my-blueprint-moderator", "Admin"],
"users": [],
"teams": [],
"ownedByTeam": true // changed from false
}
}
}
Set granular access controls to catalog data
It is possible to assign more granular permissions controls on entities:
- Update specific property
- Update specific relation
To assign permissions to update a specific entity property, give the desired persona permissions under the updateProperties -> propertyName object as shown below:
- Role
- User
- Team
- Ownership
To give property update permissions to another role, add it to the roles array:
{
"entities": {
... other permissions
"updateProperties": {
"myProperty": {
"roles": ["my-blueprint-moderator", "Admin", "my-role"], // added my-role
"users": [],
"teams": [],
"ownedByTeam": false
}
}
}
}
To give property update permissions to another user, add it to the users array:
{
"entities": {
... other permissions
"updateProperties": {
"myProperty": {
"roles": ["my-blueprint-moderator", "Admin"],
"users": ["my-user@example.com"], // added my-user@example.com
"teams": [],
"ownedByTeam": false
}
}
}
}
To give property update permissions to another team, add it to the teams array:
{
"entities": {
... other permissions
"updateProperties": {
"myProperty": {
"roles": ["my-blueprint-moderator", "Admin"],
"users": [],
"teams": ["my-team"], // added my-team
"ownedByTeam": false
}
}
}
}
Teams can be assigned to entities, denoting the team's ownership of the entity.
To give property update permissions to members of the owning team of an entity, change the ownedByTeam key:
{
"entities": {
... other permissions
"updateProperties": {
"myProperty": {
"roles": ["my-blueprint-moderator", "Admin"],
"users": [],
"teams": [],
"ownedByTeam": true // changed from false
}
}
}
}
To assign permissions to update a specific entity relation, give the desired persona permissions under the updateRelations -> relationName object as shown below:
- Role
- User
- Team
- Ownership
To give relation update permissions to another role, add it to the roles array:
{
"entities": {
... other permissions
"updateRelations": {
"myRelation": {
"roles": ["my-blueprint-moderator", "Admin", "my-role"], // added my-role
"users": [],
"teams": [],
"ownedByTeam": false
}
}
}
}
To give relation update permissions to another user, add it to the users array:
{
"entities": {
... other permissions
"updateRelations": {
"myRelation": {
"roles": ["my-blueprint-moderator", "Admin"],
"users": ["my-user@example.com"], // added my-user@example.com
"teams": [],
"ownedByTeam": false
}
}
}
}
To give relation update permissions to another team, add it to the teams array:
{
"entities": {
... other permissions
"updateRelations": {
"myRelation": {
"roles": ["my-blueprint-moderator", "Admin"],
"users": [],
"teams": ["my-team"], // added my-team
"ownedByTeam": false
}
}
}
}
Teams can be assigned to entities, denoting the team's ownership of the entity.
To give relation update permissions to members of the owning team of an entity, change the ownedByTeam key:
{
"entities": {
... other permissions
"updateRelations": {
"myRelation": {
"roles": ["my-blueprint-moderator", "Admin"],
"users": [],
"teams": [],
"ownedByTeam": true // changed from false
}
}
}
}
Software catalog RBAC examples
Refer to the examples page for practical examples of Port's RBAC.
FAQ
Since the catalog RBAC can be very granular, in some instances it might not be perfectly clear what the resulting assigned permissions would do, this part aims to provide some real-world examples and the behavior of Port's RBAC in those instances.
What happens if a user lacks the permissions to edit a required property of the blueprint?
In this case the user will not be able to register or update entities as a whole because they can't provide a value for the required property.
What happens if the ownedByTeam setting is enabled for entity registration, but the user can't edit the team property?
In this case the user will not be able to register a new entity since they can't select a value for the entity's team field and mark it as owned by their team.