Sentry
Our Sentry integration allows you to import projects, issues, project-tag and issue-tag from your Sentry cloud account into Port, according to your mapping and definition.
A Project is essentially a container for all the data and information related to a specific application or service that you want to monitor.
An Issue is a group of incidents that describe the underlying problem of your symptoms.
A Tag is a key/value pair used to attach additional metadata to objects. This metadata can include information such as the environment, runtime, log level, and more.
Common use cases
- Map your monitored projects and issues into Port.
Prerequisites
To install the integration, you need a Kubernetes cluster that the integration's container chart will be deployed to.
Please make sure that you have kubectl and helm installed on your machine, and that your kubectl CLI is connected to the Kubernetes cluster where you plan to install the integration.
If you are having trouble installing this integration, please refer to these troubleshooting steps.
Installation
Choose one of the following installation methods:
- Hosted by Port
- Real Time & Always On
- Scheduled
Using this installation option means that the integration will be hosted by Port, with a customizable resync interval to ingest data into Port.
To install, follow the following steps:
-
Go to the Data sources page of your portal.
-
Click on the
+ Data sourcebutton in the top-right corner. -
Click on the relevant integration in the list.
-
Under
Select your installation method, chooseHosted by Port. -
Configure the
integration settingsandapplication settingsas you wish (see below for details).
Application settings
Every integration hosted by Port has the following customizable application settings:
-
Resync interval: The frequency at which Port will ingest data from the integration. There are various options available, ranging from every 1 hour to once a day. -
Send raw data examples: A boolean toggle (enabledby default). If enabled, raw data examples will be sent from the integration to Port. These examples are used when testing your mapping configuration, they allow you to run yourjqexpressions against real data and see the results.
Integration settings
Every integration has its own tool-specific settings, under the Integration settings section.
Each of these settings has an ⓘ icon next to it, which you can hover over to see a description of the setting.
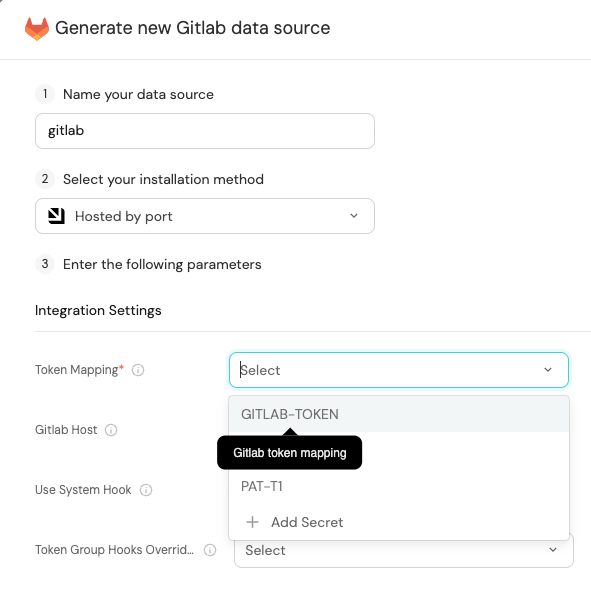
Port secrets
Some integration settings require sensitive pieces of data, such as tokens.
For these settings, Port secrets will be used, ensuring that your sensitive data is encrypted and secure.
When changing such a setting, you will be prompted to choose an existing secret or create a new one:
Currently, live events are not supported for integrations hosted by Port.
Resyncs will be performed periodically, based on the Resync interval you have configured, or manually triggered by you via Port's UI.
Therefore, real-time events such as GitOps pushes will not be ingested into Port immediately.
Live events are WIP and will be supported in the future.
Using this installation option means that the integration will be able to update Port in real time using webhooks.
This table summarizes the available parameters for the installation. Set them as you wish in the script below, then copy it and run it in your terminal:
| Parameter | Description | Required |
|---|---|---|
port.clientId | Your port client id | ✅ |
port.clientSecret | Your port client secret | ✅ |
port.baseUrl | Your Port API URL - https://api.getport.io for EU, https://api.us.getport.io for US | ✅ |
integration.identifier | Change the identifier to describe your integration | ✅ |
integration.type | The integration type | ✅ |
integration.eventListener.type | The event listener type | ✅ |
integration.secrets.sentryToken | The Sentry API token. The token requires read permissions for Projects and Issue & Event | ✅ |
integration.config.sentryHost | The Sentry host. For example https://sentry.io | ✅ |
integration.config.sentryOrganization | The Sentry organization slug. For example acme from https://acme.sentry.io | ✅ |
scheduledResyncInterval | The number of minutes between each resync | ❌ |
initializePortResources | Default true, When set to true the integration will create default blueprints and the port App config Mapping | ❌ |
- Helm
- ArgoCD
To install the integration using Helm, run the following command:
helm repo add --force-update port-labs https://port-labs.github.io/helm-charts
helm upgrade --install my-sentry-integration port-labs/port-ocean \
--set port.clientId="PORT_CLIENT_ID" \
--set port.clientSecret="PORT_CLIENT_SECRET" \
--set port.baseUrl="https://api.getport.io" \
--set initializePortResources=true \
--set integration.identifier="my-sentry-integration" \
--set integration.type="sentry" \
--set integration.eventListener.type="POLLING" \
--set integration.config.sentryHost="https://sentry.io" \
--set integration.secrets.sentryToken="string" \
--set integration.config.sentryOrganization="string"
The baseUrl, port_region, port.baseUrl, portBaseUrl, port_base_url and OCEAN__PORT__BASE_URL parameters are used to select which instance or Port API will be used.
Port exposes two API instances, one for the EU region of Port, and one for the US region of Port.
- If you use the EU region of Port, available at https://app.getport.io, your Port API URL is
https://api.getport.io - If you use the US region of Port, available at https://app.us.getport.io, your Port API URL is
https://api.us.getport.io
To install the integration using ArgoCD, follow these steps:
- Create a
values.yamlfile inargocd/my-ocean-sentry-integrationin your git repository with the content:
Remember to replace the placeholders for SENTRY_HOST SENTRY_ORGANIZATION and SENTRY_TOKEN.
initializePortResources: true
scheduledResyncInterval: 120
integration:
identifier: my-ocean-sentry-integration
type: sentry
eventListener:
type: POLLING
config:
sentryHost: SENTRY_HOST
sentryOrganization: SENTRY_ORGANIZATION
secrets:
sentryToken: SENTRY_TOKEN
- Install the
my-ocean-sentry-integrationArgoCD Application by creating the followingmy-ocean-sentry-integration.yamlmanifest:
Remember to replace the placeholders for YOUR_PORT_CLIENT_ID YOUR_PORT_CLIENT_SECRET and YOUR_GIT_REPO_URL.
Multiple sources ArgoCD documentation can be found here.
ArgoCD Application
apiVersion: argoproj.io/v1alpha1
kind: Application
metadata:
name: my-ocean-sentry-integration
namespace: argocd
spec:
destination:
namespace: my-ocean-sentry-integration
server: https://kubernetes.default.svc
project: default
sources:
- repoURL: 'https://port-labs.github.io/helm-charts/'
chart: port-ocean
targetRevision: 0.1.14
helm:
valueFiles:
- $values/argocd/my-ocean-sentry-integration/values.yaml
parameters:
- name: port.clientId
value: YOUR_PORT_CLIENT_ID
- name: port.clientSecret
value: YOUR_PORT_CLIENT_SECRET
- name: port.baseUrl
value: https://api.getport.io
- repoURL: YOUR_GIT_REPO_URL
targetRevision: main
ref: values
syncPolicy:
automated:
prune: true
selfHeal: true
syncOptions:
- CreateNamespace=true
The baseUrl, port_region, port.baseUrl, portBaseUrl, port_base_url and OCEAN__PORT__BASE_URL parameters are used to select which instance or Port API will be used.
Port exposes two API instances, one for the EU region of Port, and one for the US region of Port.
- If you use the EU region of Port, available at https://app.getport.io, your Port API URL is
https://api.getport.io - If you use the US region of Port, available at https://app.us.getport.io, your Port API URL is
https://api.us.getport.io
- Apply your application manifest with
kubectl:
kubectl apply -f my-ocean-sentry-integration.yaml
For advanced configuration such as proxies or self-signed certificates, click here.
Event listener
The integration uses polling to pull the configuration from Port every minute and check it for changes. If there is a change, a resync will occur.
- GitHub
- Jenkins
- Azure Devops
- GitLab
This workflow will run the Sentry integration once and then exit, this is useful for scheduled ingestion of data.
If you want the integration to update Port in real time you should use the Real Time & Always On installation option
Make sure to configure the following Github Secrets:
| Parameter | Description | Required |
|---|---|---|
OCEAN__INTEGRATION__CONFIG__SENTRY_TOKEN | The Sentry API token. The token requires read permissions for Projects and Issue & Event | ✅ |
OCEAN__INTEGRATION__CONFIG__SENTRY_HOST | The Sentry host. For example https://sentry.io | ✅ |
OCEAN__INTEGRATION__CONFIG__SENTRY_ORGANIZATION | The Sentry organization slug. For example acme from https://acme.sentry.io | ✅ |
OCEAN__INITIALIZE_PORT_RESOURCES | Default true, When set to false the integration will not create default blueprints and the port App config Mapping | ❌ |
OCEAN__INTEGRATION__IDENTIFIER | Change the identifier to describe your integration, if not set will use the default one | ❌ |
OCEAN__PORT__CLIENT_ID | Your port client id | ✅ |
OCEAN__PORT__CLIENT_SECRET | Your port client secret | ✅ |
OCEAN__PORT__BASE_URL | Your Port API URL - https://api.getport.io for EU, https://api.us.getport.io for US | ✅ |
Here is an example for sentry-integration.yml workflow file:
name: Sentry Exporter Workflow
# This workflow responsible for running Sentry exporter.
on:
workflow_dispatch:
jobs:
run-integration:
runs-on: ubuntu-latest
steps:
- uses: port-labs/ocean-sail@v1
with:
type: 'sentry'
port_client_id: ${{ secrets.OCEAN__PORT__CLIENT_ID }}
port_client_secret: ${{ secrets.OCEAN__PORT__CLIENT_SECRET }}
port_base_url: https://api.getport.io
config: |
sentry_token: ${{ secrets.OCEAN__INTEGRATION__CONFIG__SENTRY_TOKEN }}
sentry_host: ${{ secrets.OCEAN__INTEGRATION__CONFIG__SENTRY_HOST }}
sentry_organization: ${{ secrets.OCEAN__INTEGRATION__CONFIG__SENTRY_ORGANIZATION }}
This pipeline will run the Sentry integration once and then exit, this is useful for scheduled ingestion of data.
Your Jenkins agent should be able to run docker commands.
If you want the integration to update Port in real time using webhooks you should use the Real Time & Always On installation option.
Make sure to configure the following Jenkins Credentials of Secret Text type:
| Parameter | Description | Required |
|---|---|---|
OCEAN__INTEGRATION__CONFIG__SENTRY_TOKEN | The Sentry API token. The token requires read permissions for Projects and Issue & Event | ✅ |
OCEAN__INTEGRATION__CONFIG__SENTRY_HOST | The Sentry host. For example https://sentry.io | ✅ |
OCEAN__INTEGRATION__CONFIG__SENTRY_ORGANIZATION | The Sentry organization slug. For example acme from https://acme.sentry.io | ✅ |
OCEAN__INITIALIZE_PORT_RESOURCES | Default true, When set to false the integration will not create default blueprints and the port App config Mapping | ❌ |
OCEAN__INTEGRATION__IDENTIFIER | Change the identifier to describe your integration, if not set will use the default one | ❌ |
OCEAN__PORT__CLIENT_ID | Your port client id | ✅ |
OCEAN__PORT__CLIENT_SECRET | Your port client secret | ✅ |
OCEAN__PORT__BASE_URL | Your Port API URL - https://api.getport.io for EU, https://api.us.getport.io for US | ✅ |
Here is an example for Jenkinsfile groovy pipeline file:
pipeline {
agent any
stages {
stage('Run Sentry Integration') {
steps {
script {
withCredentials([
string(credentialsId: 'OCEAN__INTEGRATION__CONFIG__SENTRY_TOKEN', variable: 'OCEAN__INTEGRATION__CONFIG__SENTRY_TOKEN'),
string(credentialsId: 'OCEAN__INTEGRATION__CONFIG__SENTRY_HOST', variable: 'OCEAN__INTEGRATION__CONFIG__SENTRY_HOST'),
string(credentialsId: 'OCEAN__INTEGRATION__CONFIG__SENTRY_ORGANIZATION', variable: 'OCEAN__INTEGRATION__CONFIG__SENTRY_ORGANIZATION'),
string(credentialsId: 'OCEAN__PORT__CLIENT_ID', variable: 'OCEAN__PORT__CLIENT_ID'),
string(credentialsId: 'OCEAN__PORT__CLIENT_SECRET', variable: 'OCEAN__PORT__CLIENT_SECRET'),
]) {
sh('''
#Set Docker image and run the container
integration_type="sentry"
version="latest"
image_name="ghcr.io/port-labs/port-ocean-${integration_type}:${version}"
docker run -i --rm --platform=linux/amd64 \
-e OCEAN__EVENT_LISTENER='{"type":"ONCE"}' \
-e OCEAN__INITIALIZE_PORT_RESOURCES=true \
-e OCEAN__INTEGRATION__CONFIG__SENTRY_TOKEN=$OCEAN__INTEGRATION__CONFIG__SENTRY_TOKEN \
-e OCEAN__INTEGRATION__CONFIG__SENTRY_HOST=$OCEAN__INTEGRATION__CONFIG__SENTRY_HOST \
-e OCEAN__INTEGRATION__CONFIG__SENTRY_ORGANIZATION=$OCEAN__INTEGRATION__CONFIG__SENTRY_ORGANIZATION \
-e OCEAN__PORT__CLIENT_ID=$OCEAN__PORT__CLIENT_ID \
-e OCEAN__PORT__CLIENT_SECRET=$OCEAN__PORT__CLIENT_SECRET \
-e OCEAN__PORT__BASE_URL='https://api.getport.io' \
$image_name
exit $?
''')
}
}
}
}
}
}
This pipeline will run the Sentry integration once and then exit, this is useful for scheduled ingestion of data.
Your Azure Devops agent should be able to run docker commands. Learn more about agents here.
If you want the integration to update Port in real time using webhooks you should use the Real Time & Always On installation option.
Variable groups store values and secrets you'll use in your pipelines across your project. Learn more
Setting Up Your Credentials
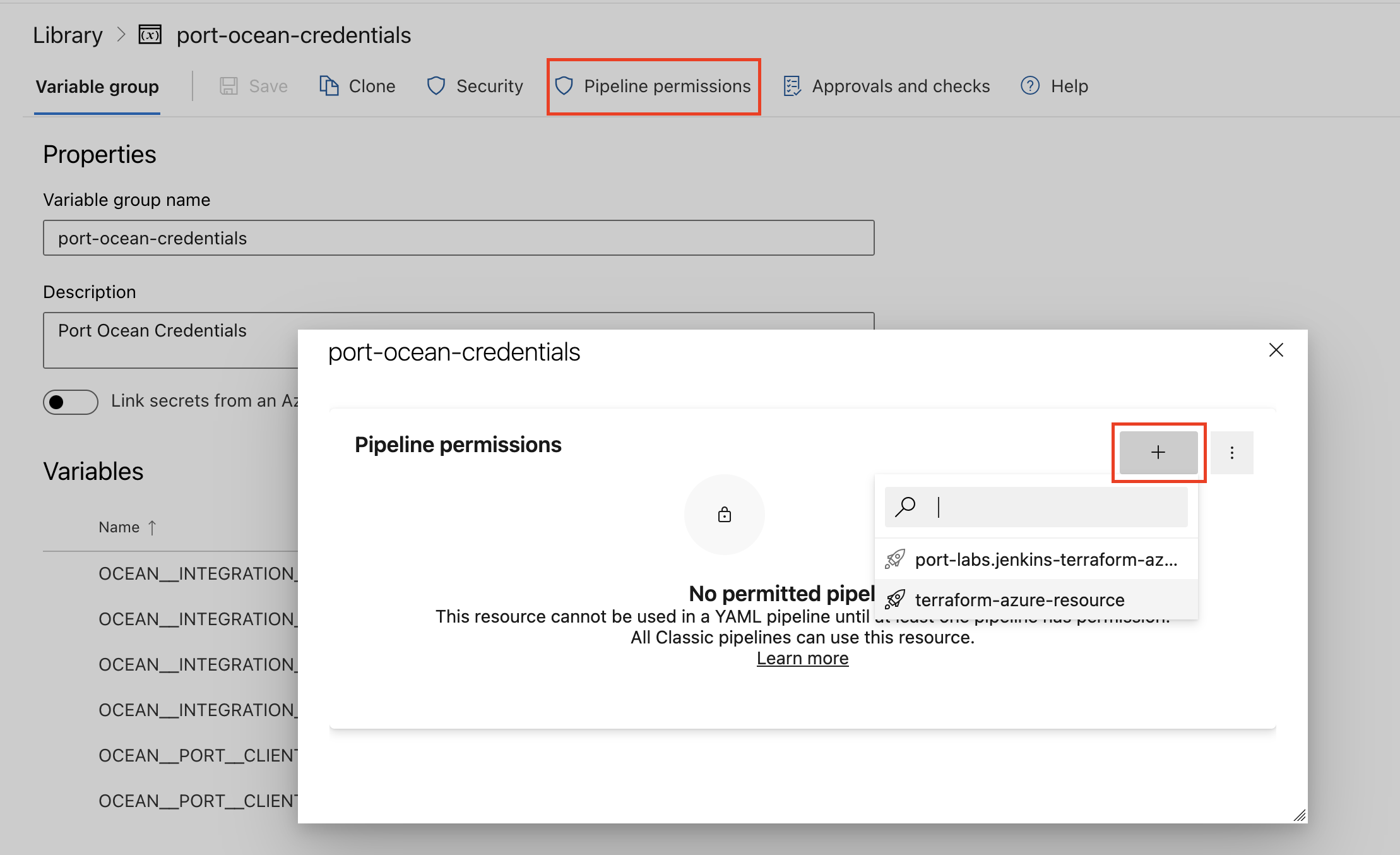
- Create a Variable Group: Name it port-ocean-credentials. Store the required variables from the table.
- Authorize Your Pipeline:
- Go to "Library" -> "Variable groups."
- Find port-ocean-credentials and click on it.
- Select "Pipeline Permissions" and add your pipeline to the authorized list.
| Parameter | Description | Required |
|---|---|---|
OCEAN__INTEGRATION__CONFIG__SENTRY_TOKEN | The Sentry API token. The token requires read permissions for Projects and Issue & Event | ✅ |
OCEAN__INTEGRATION__CONFIG__SENTRY_HOST | The Sentry host. For example https://sentry.io | ✅ |
OCEAN__INTEGRATION__CONFIG__SENTRY_ORGANIZATION | The Sentry organization slug. For example acme from https://acme.sentry.io | ✅ |
OCEAN__INITIALIZE_PORT_RESOURCES | Default true, When set to false the integration will not create default blueprints and the port App config Mapping | ❌ |
OCEAN__INTEGRATION__IDENTIFIER | Change the identifier to describe your integration, if not set will use the default one | ❌ |
OCEAN__PORT__CLIENT_ID | Your port client id | ✅ |
OCEAN__PORT__CLIENT_SECRET | Your port client secret | ✅ |
OCEAN__PORT__BASE_URL | Your Port API URL - https://api.getport.io for EU, https://api.us.getport.io for US | ✅ |
Here is an example for sentry-integration.yml pipeline file:
trigger:
- main
pool:
vmImage: "ubuntu-latest"
variables:
- group: port-ocean-credentials
steps:
- script: |
# Set Docker image and run the container
integration_type="sentry"
version="latest"
image_name="ghcr.io/port-labs/port-ocean-$integration_type:$version"
docker run -i --rm \
-e OCEAN__EVENT_LISTENER='{"type":"ONCE"}' \
-e OCEAN__INITIALIZE_PORT_RESOURCES=true \
-e OCEAN__INTEGRATION__CONFIG__SENTRY_TOKEN=$(OCEAN__INTEGRATION__CONFIG__SENTRY_TOKEN) \
-e OCEAN__INTEGRATION__CONFIG__SENTRY_HOST=$(OCEAN__INTEGRATION__CONFIG__SENTRY_HOST) \
-e OCEAN__INTEGRATION__CONFIG__SENTRY_ORGANIZATION=$(OCEAN__INTEGRATION__CONFIG__SENTRY_ORGANIZATION) \
-e OCEAN__PORT__CLIENT_ID=$(OCEAN__PORT__CLIENT_ID) \
-e OCEAN__PORT__CLIENT_SECRET=$(OCEAN__PORT__CLIENT_SECRET) \
-e OCEAN__PORT__BASE_URL='https://api.getport.io' \
$image_name
exit $?
displayName: 'Ingest Data into Port'
This workflow will run the Sentry integration once and then exit, this is useful for scheduled ingestion of data.
If you want the integration to update Port in real time using webhooks you should use the Real Time & Always On installation option.
Make sure to configure the following GitLab variables:
| Parameter | Description | Required |
|---|---|---|
OCEAN__INTEGRATION__CONFIG__SENTRY_TOKEN | The Sentry API token. The token requires read permissions for Projects and Issue & Event | ✅ |
OCEAN__INTEGRATION__CONFIG__SENTRY_HOST | The Sentry host. For example https://sentry.io | ✅ |
OCEAN__INTEGRATION__CONFIG__SENTRY_ORGANIZATION | The Sentry organization slug. For example acme from https://acme.sentry.io | ✅ |
OCEAN__INITIALIZE_PORT_RESOURCES | Default true, When set to false the integration will not create default blueprints and the port App config Mapping | ❌ |
OCEAN__INTEGRATION__IDENTIFIER | Change the identifier to describe your integration, if not set will use the default one | ❌ |
OCEAN__PORT__CLIENT_ID | Your port client id | ✅ |
OCEAN__PORT__CLIENT_SECRET | Your port client secret | ✅ |
OCEAN__PORT__BASE_URL | Your Port API URL - https://api.getport.io for EU, https://api.us.getport.io for US | ✅ |
Here is an example for .gitlab-ci.yml pipeline file:
default:
image: docker:24.0.5
services:
- docker:24.0.5-dind
before_script:
- docker info
variables:
INTEGRATION_TYPE: sentry
VERSION: latest
stages:
- ingest
ingest_data:
stage: ingest
variables:
IMAGE_NAME: ghcr.io/port-labs/port-ocean-$INTEGRATION_TYPE:$VERSION
script:
- |
docker run -i --rm --platform=linux/amd64 \
-e OCEAN__EVENT_LISTENER='{"type":"ONCE"}' \
-e OCEAN__INITIALIZE_PORT_RESOURCES=true \
-e OCEAN__INTEGRATION__CONFIG__SENTRY_TOKEN=$OCEAN__INTEGRATION__CONFIG__SENTRY_TOKEN \
-e OCEAN__INTEGRATION__CONFIG__SENTRY_HOST=$OCEAN__INTEGRATION__CONFIG__SENTRY_HOST \
-e OCEAN__INTEGRATION__CONFIG__SENTRY_ORGANIZATION=$OCEAN__INTEGRATION__CONFIG__SENTRY_ORGANIZATION \
-e OCEAN__PORT__CLIENT_ID=$OCEAN__PORT__CLIENT_ID \
-e OCEAN__PORT__CLIENT_SECRET=$OCEAN__PORT__CLIENT_SECRET \
-e OCEAN__PORT__BASE_URL='https://api.getport.io' \
$IMAGE_NAME
rules: # Run only when changes are made to the main branch
- if: '$CI_COMMIT_BRANCH == "main"'
The baseUrl, port_region, port.baseUrl, portBaseUrl, port_base_url and OCEAN__PORT__BASE_URL parameters are used to select which instance or Port API will be used.
Port exposes two API instances, one for the EU region of Port, and one for the US region of Port.
- If you use the EU region of Port, available at https://app.getport.io, your Port API URL is
https://api.getport.io - If you use the US region of Port, available at https://app.us.getport.io, your Port API URL is
https://api.us.getport.io
For advanced configuration such as proxies or self-signed certificates, click here.
Ingesting Sentry objects
The Sentry integration uses a YAML configuration to describe the process of loading data into the developer portal.
Here is an example snippet from the config which demonstrates the process for getting Issue data from Sentry:
resources:
- kind: issue
selector:
query: "true"
port:
entity:
mappings:
identifier: ".id"
title: ".title"
blueprint: '"sentryIssue"'
properties:
link: ".permalink"
status: ".status"
isUnhandled: ".isUnhandled"
relations:
project: ".project.slug"
The integration makes use of the JQ JSON processor to select, modify, concatenate, transform and perform other operations on existing fields and values from Sentry's API events.
Configuration structure
The integration configuration determines which resources will be queried from Sentry, and which entities and properties will be created in Port.
The following resources can be used to map data from Sentry, it is possible to reference any field that appears in the API responses linked below for the mapping configuration.
-
The root key of the integration configuration is the
resourceskey:resources:
- kind: project
selector:
... -
The
kindkey is a specifier for a Sentry object:resources:
- kind: project
selector:
... -
The
port,entityand themappingskeys are used to map the Sentry object fields to Port entities. To create multiple mappings of the same kind, you can add another item in theresourcesarray;resources:
- kind: project
selector:
query: "true"
port:
entity:
mappings:
identifier: .slug
title: .name
blueprint: '"sentryProject"'
properties:
dateCreated: .dateCreated
platform: .platform
status: .status
link: .organization.links.organizationUrl + "/projects/" + .name
Note the value of the blueprint key - if you want to use a hardcoded string, you need to encapsulate it in 2 sets of quotes, for example use a pair of single-quotes (') and then another pair of double-quotes (")
Ingest data into Port
To ingest Sentry objects using the integration configuration, you can follow the steps below:
- Go to the DevPortal Builder page.
- Select a blueprint you want to ingest using Sentry.
- Choose the Ingest Data option from the menu.
- Select Sentry under the APM & alerting category.
- Add the contents of your integration configuration to the editor.
- Click
Resync.
Examples
Examples of blueprints and the relevant integration configurations:
Project
Project blueprint
{
"identifier": "sentryProject",
"title": "Sentry Project",
"icon": "Sentry",
"schema": {
"properties": {
"dateCreated": {
"title": "Date Created",
"type": "string",
"format": "date-time"
},
"platform": {
"type": "string",
"title": "Platform"
},
"status": {
"title": "Status",
"type": "string",
"enum": [
"active",
"disabled",
"pending_deletion",
"deletion_in_progress"
]
},
"link": {
"title": "Link",
"type": "string",
"format": "url"
}
},
"required": []
},
"mirrorProperties": {},
"calculationProperties": {},
"relations": {}
}
Integration configuration
createMissingRelatedEntities: true
deleteDependentEntities: true
resources:
- kind: project
selector:
query: "true"
port:
entity:
mappings:
identifier: .slug
title: .name
blueprint: '"sentryProject"'
properties:
dateCreated: .dateCreated
platform: .platform
status: .status
link: .organization.links.organizationUrl + "/projects/" + .name
Issue
Issue blueprint
{
"identifier": "sentryIssue",
"title": "Sentry Issue",
"icon": "Sentry",
"schema": {
"properties": {
"link": {
"title": "Link",
"type": "string",
"format": "url"
},
"status": {
"title": "Status",
"type": "string",
"enum": [
"resolved",
"unresolved",
"ignored",
"reprocessing"
],
"enumColors": {
"resolved": "green",
"unresolved": "red",
"ignored": "lightGray",
"reprocessing": "yellow"
}
},
"isUnhandled": {
"title": "isUnhandled",
"type": "boolean"
}
},
"required": []
},
"mirrorProperties": {},
"calculationProperties": {},
"relations": {
"projectEnvironment": {
"title": "Sentry Project",
"target": "sentryProject",
"required": false,
"many": true
}
}
}
Integration configuration
createMissingRelatedEntities: true
deleteDependentEntities: true
resources:
- kind: issue
selector:
query: "true"
port:
entity:
mappings:
identifier: ".id"
title: ".title"
blueprint: '"sentryIssue"'
properties:
link: ".permalink"
status: ".status"
isUnhandled: ".isUnhandled"
relations:
project: ".project.slug"
Project Environment
Project environment blueprint
{
"identifier": "sentryProject",
"title": "Sentry Project Environment",
"icon": "Sentry",
"schema": {
"properties": {
"dateCreated": {
"title": "Date Created",
"type": "string",
"format": "date-time"
},
"platform": {
"type": "string",
"title": "Platform"
},
"status": {
"title": "Status",
"type": "string",
"enum": [
"active",
"disabled",
"pending_deletion",
"deletion_in_progress"
]
},
"link": {
"title": "Link",
"type": "string",
"format": "url"
}
},
"required": []
},
"mirrorProperties": {},
"calculationProperties": {},
"relations": {}
}
Integration configuration
Theselector.tag key in the project-tag kind defines which Sentry tag data is synced to Port. In the configuration provided below, you will ingest all environment tag from your Sentry account to Port. For instance, if a Sentry project has 3 environments namely development, staging and production, this configuration will create 3 entities in the Sentry Project Environment catalog. You will then use the issue-tag kind to connect each issue to its environment.
createMissingRelatedEntities: true
deleteDependentEntities: true
resources:
- kind: project-tag
selector:
query: "true"
tag: "environment"
port:
entity:
mappings:
identifier: .slug + "-" + .__tags.name
title: .name + "-" + .__tags.name
blueprint: '"sentryProject"'
properties:
dateCreated: .dateCreated
platform: .platform
status: .status
link: .organization.links.organizationUrl + "/projects/" + .name
- kind: issue-tag
selector:
query: "true"
tag: "environment"
port:
entity:
mappings:
identifier: .id
title: .title
blueprint: '"sentryIssue"'
properties:
link: .permalink
status: .status
isUnhandled: .isUnhandled
relations:
projectEnvironment: '[(.project.slug as $slug | .__tags[] | "\($slug)-\(.name)")]'
Let's Test It
This section includes a sample response data from Sentry. In addition, it includes the entity created from the resync event based on the Ocean configuration provided in the previous section.
Payload
Here is an example of the payload structure from Sentry:
Project response data
{
"id": "4504931759095808",
"slug": "python-fastapi",
"name": "python-fastapi",
"platform": "python-fastapi",
"dateCreated": "2023-03-31T06:18:37.290732Z",
"isBookmarked": false,
"isMember": false,
"features": [
"alert-filters",
"minidump",
"race-free-group-creation",
"similarity-indexing",
"similarity-view",
"span-metrics-extraction",
"span-metrics-extraction-resource",
"releases"
],
"firstEvent": "2023-03-31T06:25:54.666640Z",
"firstTransactionEvent": false,
"access": [],
"hasAccess": true,
"hasMinifiedStackTrace": false,
"hasMonitors": false,
"hasProfiles": false,
"hasReplays": false,
"hasFeedbacks": false,
"hasSessions": false,
"isInternal": false,
"isPublic": false,
"avatar": {
"avatarType": "letter_avatar",
"avatarUuid": null
},
"color": "#913fbf",
"status": "active",
"organization": {
"id": "4504931754901504",
"slug": "test-org",
"status": {
"id": "active",
"name": "active"
},
"name": "Test Org",
"dateCreated": "2023-03-31T06:17:33.619189Z",
"isEarlyAdopter": false,
"require2FA": false,
"requireEmailVerification": false,
"avatar": {
"avatarType": "letter_avatar",
"avatarUuid": null,
"avatarUrl": null
},
"features": [
"performance-tracing-without-performance",
"performance-consecutive-http-detector",
"performance-large-http-payload-detector",
"escalating-issues",
"minute-resolution-sessions",
"performance-issues-render-blocking-assets-detector",
"event-attachments"
],
"links": {
"organizationUrl": "https://test-org.sentry.io",
"regionUrl": "https://us.sentry.io"
},
"hasAuthProvider": false
}
}
Issue response data
{
"id": "4605173695",
"shareId": "None",
"shortId": "PYTHON-FASTAPI-2",
"title": "ZeroDivisionError: division by zero",
"culprit": "index",
"permalink": "https://test-org.sentry.io/issues/4605173695/",
"logger": "None",
"level": "error",
"status": "unresolved",
"statusDetails": {},
"substatus": "new",
"isPublic": false,
"platform": "python",
"project": {
"id": "4504931759095808",
"name": "python-fastapi",
"slug": "python-fastapi",
"platform": "python-fastapi"
},
"type": "error",
"metadata": {
"value": "division by zero",
"type": "ZeroDivisionError",
"filename": "app.py",
"function": "index",
"display_title_with_tree_label": false,
"in_app_frame_mix": "mixed"
},
"numComments": 0,
"assignedTo": "None",
"isBookmarked": false,
"isSubscribed": false,
"subscriptionDetails": "None",
"hasSeen": false,
"annotations": [],
"issueType": "error",
"issueCategory": "error",
"isUnhandled": true,
"count": "1",
"userCount": 0,
"firstSeen": "2023-11-06T08:31:27.058163Z",
"lastSeen": "2023-11-06T08:31:27.058163Z",
"stats": {
"24h": [
[1699174800, 0],
[1699178400, 0],
[1699182000, 0],
[1699250400, 0],
[1699254000, 0],
[1699257600, 1]
]
}
}
Project environment response data
{
"id":"4504931759095808",
"slug":"python-fastapi",
"name":"python-fastapi",
"platform":"python-fastapi",
"dateCreated":"2023-03-31T06:18:37.290732Z",
"isBookmarked":false,
"isMember":false,
"features":[
"alert-filters",
"minidump",
"race-free-group-creation",
"similarity-indexing",
"similarity-view",
"span-metrics-extraction",
"span-metrics-extraction-resource",
"releases"
],
"firstEvent":"2023-03-31T06:25:54.666640Z",
"firstTransactionEvent":false,
"access":[
],
"hasAccess":true,
"hasMinifiedStackTrace":false,
"hasMonitors":false,
"hasProfiles":false,
"hasReplays":false,
"hasFeedbacks":false,
"hasSessions":false,
"isInternal":false,
"isPublic":false,
"avatar":{
"avatarType":"letter_avatar",
"avatarUuid":null
},
"color":"#913fbf",
"status":"active",
"organization":{
"id":"4504931754901504",
"slug":"pages-org",
"status":{
"id":"active",
"name":"active"
},
"name":"Pages Org",
"dateCreated":"2023-03-31T06:17:33.619189Z",
"isEarlyAdopter":false,
"require2FA":false,
"requireEmailVerification":false,
"avatar":{
"avatarType":"letter_avatar",
"avatarUuid":null,
"avatarUrl":null
},
"links":{
"organizationUrl":"https://pages-org.sentry.io",
"regionUrl":"https://us.sentry.io"
},
"hasAuthProvider":false
},
"__tags":{
"key":"environment",
"name":"production",
"value":"production",
"count":10,
"lastSeen":"2024-03-04T17:17:33Z",
"firstSeen":"2024-03-04T17:14:22Z"
}
}
Mapping Result
The combination of the sample payload and the Ocean configuration generates the following Port entity:
Project entity in Port
{
"identifier": "python-fastapi",
"title": "python-fastapi",
"icon": null,
"blueprint": "sentryProject",
"team": [],
"properties": {
"dateCreated": "2023-03-31T06:18:37.290732Z",
"platform": "python-fastapi",
"status": "active",
"link": "https://test-org.sentry.io/projects/python-fastapi"
},
"relations": {},
"createdAt": "2023-11-06T08:49:17.700Z",
"createdBy": "hBx3VFZjqgLPEoQLp7POx5XaoB0cgsxW",
"updatedAt": "2023-11-06T08:59:11.446Z",
"updatedBy": "hBx3VFZjqgLPEoQLp7POx5XaoB0cgsxW"
}
Issue entity in Port
{
"identifier": "4605173695",
"title": "ZeroDivisionError: division by zero",
"icon": null,
"blueprint": "sentryIssue",
"team": [],
"properties": {
"link": "https://test-org.sentry.io/issues/4605173695/",
"status": "unresolved",
"isUnhandled": true
},
"relations": {
"project": "python-fastapi"
},
"createdAt": "2023-11-06T08:49:20.406Z",
"createdBy": "hBx3VFZjqgLPEoQLp7POx5XaoB0cgsxW",
"updatedAt": "2023-11-06T08:49:20.406Z",
"updatedBy": "hBx3VFZjqgLPEoQLp7POx5XaoB0cgsxW"
}
Project environment entity in Port
{
"identifier": "python-fastapi-production",
"title": "python-fastapi-production",
"icon": null,
"blueprint": "sentryProject",
"team": [],
"properties": {
"dateCreated": "2023-03-31T06:18:37.290732Z",
"platform": "python-fastapi",
"status": "active",
"link": "https://test-org.sentry.io/projects/python-fastapi"
},
"relations": {},
"createdAt": "2024-03-07T12:18:17.111Z",
"createdBy": "hBx3VFZjqgLPEoQLp7POx5XaoB0cgsxW",
"updatedAt": "2024-03-07T12:31:52.041Z",
"updatedBy": "hBx3VFZjqgLPEoQLp7POx5XaoB0cgsxW"
}
Alternative installation via webhook
While the Ocean integration described above is the recommended installation method, you may prefer to use a webhook to ingest data from Sentry. If so, use the following instructions:
Webhook installation (click to expand)
In this example you are going to create a webhook integration between Sentry and Port, which will ingest issues entities.
Port configuration
Create the following blueprint definition:
Sentry issue blueprint
{
"identifier": "sentryIssue",
"description": "This blueprint represents an issue trigger event from Sentry",
"title": "Sentry Issue Event",
"icon": "Sentry",
"schema": {
"properties": {
"level": {
"type": "string",
"title": "Level",
"enum": ["error", "info", "fatal", "warning", "debug", "sample"]
},
"platform": {
"type": "string",
"title": "Platform",
"description": "the platform name in Sentry"
},
"status": {
"type": "string",
"title": "Issue Status"
},
"projectID": {
"type": "string",
"title": "Project ID",
"description": "the ID of the project in Sentry"
},
"action": {
"type": "string",
"title": "Action",
"enum": ["created", "resolved", "assigned", "ignored"]
}
},
"required": []
},
"mirrorProperties": {},
"calculationProperties": {},
"relations": {}
}
Create the following webhook configuration using Port UI:
Sentry issue webhook configuration
-
Basic details tab - fill the following details:
- Title :
Sentry issue mapper; - Identifier :
sentry_issue_mapper; - Description :
A webhook configuration to map Sentry Issues to Port; - Icon :
Sentry;
- Title :
-
Integration configuration tab - fill the following JQ mapping:
[
{
"blueprint": "sentryIssue",
"entity": {
"identifier": ".body.data.issue.id",
"title": ".body.data.issue.title",
"properties": {
"action": ".body.action",
"level": ".body.data.issue.level",
"platform": ".body.data.issue.platform",
"status": ".body.data.issue.status",
"projectID": ".body.data.issue.project.id"
}
}
}
] -
Scroll down to Advanced settings and input the following details:
- Signature Header Name :
sentry-hook-signature; - Signature Algorithm : Select
sha256from dropdown option; - Click Save at the bottom of the page.
- Signature Header Name :
We have left out the secret field from the security object in the webhook configuration because the secret value is generated by Sentry when creating the webhook.
So when following this example, please first create the webhook configuration in Port. Use the webhook URL from the response and create the webhook in Sentry.
After getting the secret from Sentry, you can go back to Port and update the webhook configuration with the secret.
Create a webhook in Sentry
- Log in to Sentry with your organization's credentials;
- Click the gear icon (Setting) at the left sidebar of the page;
- Choose Developer Settings;
- At the upper corner of this page, click on Create New Integration;
- Sentry provides two types of integrations: Internal and Public. For the purpose of this guide, choose Internal Integration and click on the Next button;
- Input the following details:
Name- use a meaningful name such as Port Webhook;Webhook URL- enter the value of theurlkey you received after creating the webhook configuration;Overview- enter a description for the webhook;Permissions- Grant your webhook Read permissions for the Issue & Event category;Webhooks- Under this section, enable the issues checkbox to allow Sentry to report issue events to Port;
- Click Save Changes at the bottom of the page.
Now that the webhook is created, you can take the secret value generated by Sentry and use it to update the security object in your Port webhook configuration
Relate comments to Issues
The following example adds a sentryComment blueprint, in addition to the sentryIssue blueprint shown in the previous example. In addition, it also adds a sentryIssue relation. The webhook will create or update the relation between the 2 existing entities, allowing you to map which issue a comment is made on:
Sentry comments blueprint (including the sentryIssue relation)
{
"identifier": "sentryComment",
"description": "This blueprint represents a Sentry comment in our software catalog",
"title": "Sentry Comment",
"icon": "Sentry",
"schema": {
"properties": {
"action": {
"type": "string",
"title": "action",
"enum": ["created", "updated", "deleted"]
},
"comment": {
"type": "string",
"title": "Comment"
},
"project": {
"type": "string",
"title": "Project Slug"
},
"issue_id": {
"type": "string",
"title": "Issue ID"
},
"timestamp": {
"type": "string",
"title": "Comment Timestamp"
}
},
"required": []
},
"mirrorProperties": {},
"calculationProperties": {},
"relations": {
"sentryIssue": {
"title": "Issue",
"target": "sentryIssue",
"required": false,
"many": false
}
}
}
Create the following webhook configuration using Port UI:
Sentry comments webhook configuration
-
Basic details tab - fill the following details:
- Title :
Sentry comment mapper; - Identifier :
sentry_comment_mapper; - Description :
A webhook configuration to map Sentry Comments to Port; - Icon :
Sentry;
- Title :
-
Integration configuration tab - fill the following JQ mapping:
[
{
"blueprint": "sentryComment",
"entity": {
"identifier": ".body.data.comment_id",
"title": "Comment Event",
"properties": {
"action": ".body.action",
"comment": ".body.data.comment",
"project": ".body.data.project_slug",
"issue_id": ".body.data.issue_id",
"timestamp": ".body.data.timestamp"
},
"relations": {
"sentryIssue": ".body.data.issue_id | tostring"
}
}
}
] -
Scroll down to Advanced settings and input the following details:
- Signature Header Name :
sentry-hook-signature; - Signature Algorithm : Select
sha256from dropdown option; - Click Save at the bottom of the page.
- Signature Header Name :
In order to view the different payloads and events available in Sentry webhooks, click here
Done! any issue and comment in Sentry will trigger a webhook event. Port will parse the events according to the mapping and update the catalog entities accordingly.
Let's Test It
This section includes a sample webhook event sent from Sentry when an issue or comment is created. In addition, it includes the entity created from the event based on the webhook configuration provided in the previous section.
Payload
Here is an example of the payload structure sent to the webhook URL when a Sentry issue or comment is created:
Sentry issue webhook event payload
{
"action": "created",
"installation": {
"uuid": "54a3e698-f389-4d86-b9f8-50093a228449"
},
"data": {
"issue": {
"id": "4253613038",
"shareId": "None",
"shortId": "PYTHON-B",
"title": "NameError: name 'total' is not defined",
"culprit": "__main__ in <module>",
"permalink": "None",
"logger": "None",
"level": "error",
"status": "unresolved",
"statusDetails": {},
"substatus": "new",
"isPublic": false,
"platform": "python",
"project": {
"id": "4504989602480128",
"name": "python",
"slug": "python",
"platform": "python"
},
"type": "error",
"metadata": {
"value": "name 'total' is not defined",
"type": "NameError",
"filename": "sentry.py",
"function": "<module>",
"display_title_with_tree_label": false
},
"numComments": 0,
"assignedTo": "None",
"isBookmarked": false,
"isSubscribed": false,
"subscriptionDetails": "None",
"hasSeen": false,
"annotations": [],
"issueType": "error",
"issueCategory": "error",
"isUnhandled": true,
"count": "1",
"userCount": 0,
"firstSeen": "2023-06-15T17:10:09.914274Z",
"lastSeen": "2023-06-15T17:10:09.914274Z"
}
},
"actor": {
"type": "application",
"id": "sentry",
"name": "Sentry"
}
}
Sentry comment webhook event payload
{
"action": "created",
"installation": {
"uuid": "d5a2de51-0138-496a-8e79-c17747c3a40d"
},
"data": {
"comment_id": "1729635072",
"issue_id": "4253613038",
"project_slug": "python",
"timestamp": "2023-06-15T17:15:53.383120Z",
"comment": "Hello admin please take a look at this"
},
"actor": {
"type": "user",
"id": 2683666,
"name": "user@domain.com"
}
}
Mapping Result
The combination of the sample payload and the webhook configuration generates the following Port sentryIssue entity:
{
"identifier": "4253613038",
"title": "NameError: name 'total' is not defined",
"blueprint": "sentryIssue",
"properties": {
"action": "created",
"level": "error",
"platform": "python",
"status": "unresolved",
"projectID": "4504989602480128"
},
"relations": {}
}
In addition, the following Port sentryComment entity will be generated:
{
"identifier": "1729635072",
"title": "Comment Event",
"blueprint": "sentryComment",
"properties": {
"action": "created",
"comment": "Hello admin please take a look at this",
"project": "python",
"issue_id": "4253613038",
"timestamp": "2023-06-15T17:15:53.383120Z"
},
"relations": {
"sentryIssue": "4253613038"
}
}