Create GitHub Secret
This example demonstrates how to create GitHub Secrets in your GitHub repository via Port Actions.
In this example we are using a pre-defined GitHub Action from GitHub Marketplace called Create GitHub Secret Action.
Example - Create GitHub Secret
Follow these steps to get started:
-
Create the following GitHub Action secrets:
-
PERSONAL_ACCESS_TOKEN- a Classic Personal Access Token with the following scopes: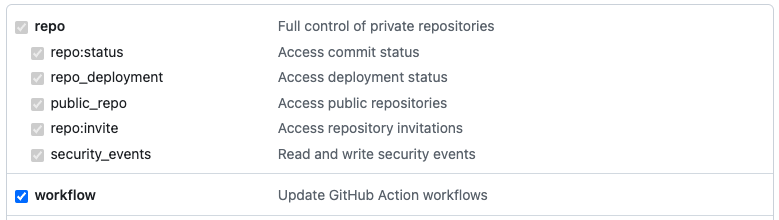
-
PORT_CLIENT_ID- Port Client ID learn more. -
PORT_CLIENT_SECRET- Port Client Secret learn more.
-
-
Install Port's GitHub app by clicking here.
-
Create a Port blueprint with the following properties:
Keep in mind this can be any blueprint you would like and this is just an example.
{
"identifier": "githubsecret",
"title": "GitHubSecret",
"icon": "Github",
"schema": {
"properties": {
"secret_key": {
"icon": "DefaultProperty",
"title": "Secret Key",
"type": "string",
"description": "All Uppercase",
"pattern": "^[^a-z]*$"
},
"secret_value": {
"icon": "DefaultProperty",
"title": "Secret Value",
"type": "string"
}
},
"required": ["secret_key", "secret_value"]
},
"mirrorProperties": {},
"calculationProperties": {},
"relations": {}
}
- Create a Port action using the following JSON definition:
Make sure to replace the placeholders for GITHUB_ORG_NAME and GITHUB_REPO_NAME in your Port Action to match your GitHub environment.
[
{
"identifier": "create_github_secret",
"title": "Create GitHub Secret",
"icon": "Github",
"userInputs": {
"properties": {
"secret_key": {
"icon": "DefaultProperty",
"title": "Secret Key",
"type": "string",
"pattern": "^[^a-z]*$"
},
"secret_value": {
"icon": "DefaultProperty",
"title": "Secret Value",
"type": "string",
"encryption": "aes256-gcm"
}
},
"required": ["secret_key", "secret_value"],
"order": ["secret_key", "secret_value"]
},
"invocationMethod": {
"type": "GITHUB",
"omitPayload": false,
"omitUserInputs": false,
"reportWorkflowStatus": true,
"org": "<GITHUB_ORG_NAME>",
"repo": "<GITHUB_REPO_NAME>",
"workflow": "create-repo-secret.yml"
},
"trigger": "CREATE",
"description": "Creates a GitHub secret in my repository",
"requiredApproval": false
}
]
- Create a workflow file under
.github/workflows/create-repo-secret.ymlwith the following content:
name: Create Repository Secret
on:
workflow_dispatch:
inputs:
secret_key:
type: string
description: Name of the secret's key
secret_value:
type: string
description: value of the secret
port_payload:
required: false
description:
Port's payload, including details for who triggered the action and
general context (blueprint, run id, etc...)
type: string
jobs:
create_secret:
runs-on: ubuntu-latest
steps:
- uses: gliech/create-github-secret-action@v1
with:
name: ${{ inputs.secret_key }}
value: ${{ inputs.secret_value }}
pa_token: ${{ secrets.PERSONAL_ACCESS_TOKEN }}
- name: UPSERT Entity
uses: port-labs/port-github-action@v1
with:
identifier: ${{ inputs.secret_key }}
title: ${{ inputs.secret_key }}
team: "[]"
icon: DefaultBlueprint
blueprint: ${{ fromJson(inputs.port_payload).context.blueprint }}
properties: |-
{
"secret_key": "${{ inputs.secret_key }}",
"secret_value": "${{ inputs.secret_value }}"
}
relations: "{}"
clientId: ${{ secrets.PORT_CLIENT_ID }}
clientSecret: ${{ secrets.PORT_CLIENT_SECRET }}
operation: UPSERT
runId: ${{ fromJson(inputs.port_payload).context.runId }}
- Trigger the action from the Self-service tab of your Port application.